Requirements for Research Security Programs per NSPM-33
Northeastern University Research Enterprises Services (NU-RES) serves as the centralized hub for assisting faculty in preparing and submitting their research and sponsored proposals. For matters regarding research integrity, research misconduct, and research security, the NU-RES Compliance team helps researchers navigate foreign collaborations and engagements while protecting their work from foreign influence. The NU-RES Compliance team coordinates with IT to ensure that all researchers are completing the required training and abiding by research security rules and regulations regarding controlled unclassified information (CUI), technology and export controls.
The purpose of NSPM-33 is to “provide guidance to Federal departments and agencies regarding their implementation of National Security Presidential Memorandum 33 on National Security Strategy for U.S. Government-Supported Research and Development”. The guidance requires a certification from research institutions awarded more than $50 million per year in total Federal research funding confirming that they have implemented a research security program meeting the four requirements highlighted in NSPM-33: Cybersecurity, Foreign Travel Security, Research Security Training, and Export Control Training (see pgs. 18-20). Northeastern is currently working to fulfill all the requirements set forth by the National Security Presidential Memorandum (NSPM-33) and its supporting (draft) Research Security Programs Standard Requirement document as released by the Office of Science and Technology (OSTP).
What is Research Security?
Research security is a broad term that refers primarily to national security concerns surrounding research involving certain types of sensitive data, intellectual property, export-controlled information, and other risks. Foreign government interference threatens the U.S. science and technology (S&T) research ecosystem and the U.S. research community by undermining the principles and values foundational to the conduct of research, and the openness necessary for the research enterprise to thrive.
Research Security Program at NU
As a global research institution, Northeastern University encourages collaboration with investigators at other institutions, both domestic and internationally. However, it is important for all investigators to be aware of and take steps to ensure that foreign influence does not threaten the integrity of research. The NU-RES Compliance team is here to help researchers navigate foreign collaborations and engagements while protecting their work from foreign influence. Northeastern University committed to providing the necessary guidance, education, and support to its faculty engaged in research. The components of Northeastern University’s research security program are below. NU-RES Compliance collaborates with various university offices to maintain a robust and up-to-date research security program.
Questions about the Research Security Program at NU? Contact our Chief Research Operations Officer, Amanda Humphrey: a.humphrey@northeastern.edu.
Cybersecurity
Research Compliance works heavily with Northeastern’s Office of Information Security to assist researchers in safeguarding their research data and information. For more information regarding the purpose, principles, and resources for cybersecurity at Northeastern, please visit the below websites:
Digital Persistent Identifiers (DPIs) & Digital CVs
Digital Persistent Identifiers (DPIs) and Digital CVs make it easier for researchers to create and maintain a complete and up to date record of their publications and achievements in one location, thereby streamlining the grant proposal process.
Northeastern is a full member of ORCID – Open Research and Contributor ID – a platform that provides a free and unique DPI for individuals engaged in research, scholarship, and innovation activities globally.
Science Experts Network Curriculum Vitae (SciENcv) is an electronic system created by the National Center for Biotechnology Information (NCBI) that allows researchers to assemble their professional information needed for participation in federally funded research. SciENcv is a digital CV that documents information regarding education, employment, honors, publications, and research grants. SciENcv will become mandatory for any NSF funded research beginning October 23, 2023, as outlined in the NSF PAPPG 2023.
More information on ORCID and SciENcv can be found here.
Disclosure Management
As stated above, disclosure and transparency surrounding relationships with, and research support from, foreign entities have been identified by the federal government as key to managing and protecting the security of our research. Prior to engaging in any international collaborations or outside activities Researchers are expected to:
- Be thorough and complete in accounting for all forms of research support, including from foreign sources and gifts, in the NIH’s other support, the NSF’s current and pending, and similar documentation submitted to other sponsors.
- Disclose financial interests and outside professional activities in eCD, the University’s Electronic Conflict Disclosure System annually, at the time of proposal submission through Northeastern University’s Research Enterprise Services (NU-RES), and within 30 days of acquiring new interests as required by the Policy on Conflict of Interest and Commitment.
- Activities requiring disclosure include support from foreign governments and foreign academic institutions, domestic and foreign consulting relationships, visiting positions at domestic and foreign institutions, investment in a start-up company, etc.
- Research Compliance is available to provide additional guidance on what you need to disclose and how and when to make a disclosure. In addition, faculty and staff should refresh their understanding of the Policy on Conflict of Interest and Commitment.
- Discuss any invitation for any academic appointment or position at another domestic or international institution (visiting, honorary, or other) with your Dean’s Office prior to accepting the appointment, as required by the Northeastern’s Faculty Handbook and Policy on Conflict of Interest and Commitment.
- Disclose to Research Compliance and College Dean’s Office any involvement in any foreign recruitment or “talent” programs. These programs are of particular interest to the federal government, due to the potential risk of undermining U.S. economic and security interests.
- Ensure compliance with the federal Foreign Corrupt Practices Act and the University’s Policy on the Foreign Corrupt Practices Act.
Export Controls
The Export Control Officer maintains responsibility for enforcing University-wide export compliance policies, procedures, and guidelines designed to meet or exceed the requirements of the various federal laws governing the export of goods, technology, and information, including compliance with ITAR, EAR, and OFAC regulations.
More information about Export Controls at NU can be found here.
Click here to access the Export Control Decision Tree.
Questions on export controls? Contact us at exportcontrols@northeastern.edu.
Related policies: Policy on Export Controls
Foreign Visitors & International Engagements
As a global university, Northeastern prides itself on its breadth of international students and faculty and encourages international engagements. Prior to hosting any foreign visitors and/or participating in any international collaborations or activities, faculty should review the below definitions and risk mitigation techniques.
Faculty must comply with the university’s Policy on External International Engagements and the international engagement approval process. Faculty are required to complete the International Engagements Intake Form and review these FAQs about the approval process, which includes roles and responsibilities and the rationale behind the policy. Please visit the International Engagements page to access the intake form.
Please make sure to review information regarding Foreign Talent Recruitment Programs.
Foreign Travel Security
NU-RES Research Compliance works with the Global Safety and Support Network to ensure that students, faculty and staff traveling internationally have the most accurate information and guidance ahead of their trip. The network provides detailed travel compliance information including travel protocols, connectivity requirements and lists of high-risk countries and high cyber risk destinations.
For international travel, students, faculty and staff are required to complete an Acknowledgement of Risk (AOR) form prior to departure, which requires disclosure of travel details, including identification of the Host or Sponsoring Institution, Organization, Department/College or Person. Information on AOR forms can be found here.
To request a loaner device (i.e. laptop) for travel to a high-risk country, please submit a ticket to the IT Service Desk here.
Travel briefings regarding research security and best practices for international travel may be required.
Related policies:
Policy on Travel and Expense Reimbursement
Policy Requiring Registration of University Travel
Policy on Travel to High-Risk and Sanctioned Destinations
Policy on Computers and Mobile Devices for Travel to Destinations with Heightened Cybersecurity Risk
Research Security & Transparency
Research Security & International Collaboration Authorship FAQs
Data Management & Sharing Plans (DMSP)
Generative AI in Research FAQ
NIH Policy Guidance for Subaward/Consortium Written Agreements
Research Integrity & Misconduct
What is Research Integrity
In addition to our robust RCR training program (insert link to RCR) we handle other research integrity matters, including allegations of plagiarism, as well as authorship disputes. Please see this guidance document which outlines how we assess authorship disputes versus matters of plagiarism.
Research Misconduct
Northeastern University is committed to the fair and thorough investigation of Research Misconduct allegations. Research misconduct is defined in accordance with federal policy as:
- Fabrication: The making up of data or results and the recording or reporting them;
- Falsification: The manipulation of research materials, equipment or processes, or the change or omission of data or results such that the research is not accurately represented in the research record;
- Plagiarism: The appropriation of another person’s ideas, processes, results or words without giving appropriate credit.
Research misconduct does not include honest error or differences of opinion. Any individual with reason to believe that research misconduct has possibly occurred must report the matter to University officials. To report a concern, email researchcompliance@northeastern.edu or contact the EthicsPoint confidential and anonymous reporting hotline.
For information on Northeastern’s process for responding to and handling allegations of research misconduct, please read our Procedures for Responding to Alleged Research Misconduct
Related Policies
Risk Mitigation Policies
What is risk mitigation?
Risks may affect overseas partners differently, and it is important to have policies in place that acknowledge and assess the existence of these risks. Some risk mitigation policy recommendations include:
- Undertaking regular due diligence on overseas partners,
- Recognizing the risks related to institutional autonomy and academic freedom overseas,
- Balancing requirements for local autonomy with robust, centralized risk management,
- Establishing clear reporting lines for communication with local stakeholders,
- Developing an exit strategy that is supported by a comprehensive, rules-based arrangement and high-level principles.
How does IP theft factor in?
Faculty should also be aware of intellectual property (IP) theft attempts. IP includes all exclusive rights to intellectual creations. All research can be at risk, but areas around applied research are particularly vulnerable. The consequence of research outcomes being exploited could be far greater and could result in the loss of intellectual property and misuse of research.
For individual researchers, interference with (or loss of) research is likely to limit their ability to publish first or take credit for the resulting intellectual property. This could potentially affect a researcher’s reputation and ability to demonstrate the impact of their research.
Hostile states target universities to steal personal data, research data and IP with the hopes that it could be used to help their own military, commercial and authoritarian interests.
Research funding organizations and private companies are important stakeholders when it comes to research that may result in the development of intellectual property. They may impose dissemination and/or publication restrictions to ensure the IP is protected. Some tips on limiting IP theft are below:
Collaboration Engagement Risk
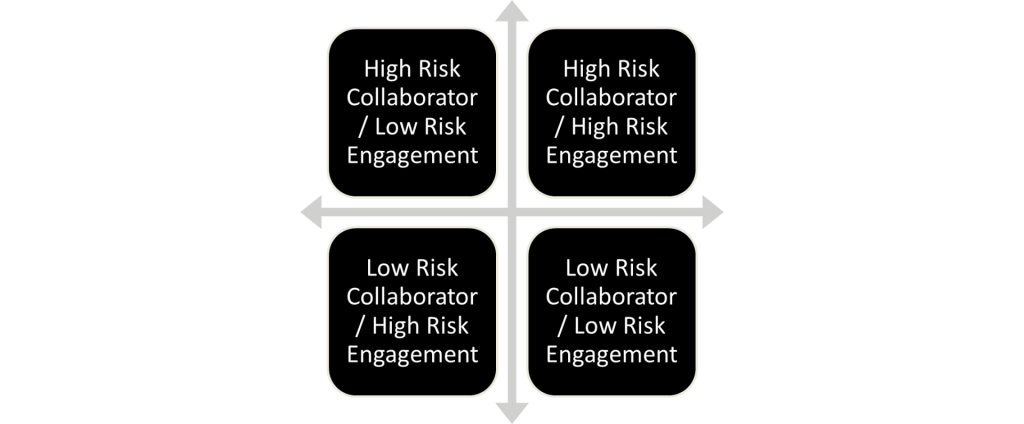
Faculty should consider what risks come with partnering with the collaborator (ex. High risk country) and the risk of the engagement (ex. What is being studied or researched?). The below risk matrix illustrates how faculty should understand the relationship and the risks that will come from collaboration with a certain individual, institution, or company, and should serve as a starting point in the process of determining if a collaboration is low or high risk.
Definitions
Due Diligence
Conducting robust checks on potential collaborators (individuals or organizations) to ensure all parties are aligned in their goals and ethical standards.
Foreign Interference (FI)
Activities carried out by, or on behalf of, a foreign state-level actor, which are coercive, covert, deceptive, or corrupt and are contrary to the sovereignty, values, and interests of another sovereign nation-state. FI does not have to be executed by a person with direct ties to the foreign state in question and should be considered without regard to national origin, race, etc. FI is possible with non-hostile actors.
Internationalization
Internationalization describes the purposeful integration of international and intercultural dimensions into aspects of university activity.
Influence vs. Interference
| Influence | Interference |
| Reciprocity in the relationship | Unlawful retrieval of information |
| Transparent flow of information (Open Science) | Lack of transparency |
| Open disagreement is permissible (freedom of speech) | Undermine values that run contrary to state policy (i.e., misinformation or restriction on speech) |
| Influence of policy through dialogue and exchange | Influence policy by bribing or otherwise silencing dissenters |
Related Government Guidance & Policies
2024
2023
2021-2022
2019-2020
- DRAFT Research Security Programs Standard Requirement (Feb 2023)
- JASON Report Research Program on Research Security (Mar 2023)
- COGR Matrix of Science & Security Laws, Regulations, & Policies (last updated Nov 2023)
- NSTC NSPM-33 Implementation Guidance Disclosure Requirements & Standardization (Nov 2023)
- NSPM-33 Implementation Guidance Definitions (Nov 2023)
- NSTC – Recommended Practices for Strengthening the Security & Integrity of America’s Science & Technology Research Enterprise (Jan 2021)
- NSPM-33 Implementation Guidance (Jan 2022)
- DOE Current & Pending Support Disclosure Requirements for Financial Assistance (Jun 2022)
- G7 Common Values and Principles on Research Security and Research Integrity (Jun 2022)
- CHIPS & Science Act (Aug 2022)
Other
- NIH Requirements for Disclosure of Other Support, Foreign Components and Conflicts of Interest
- UK Trusted Research
- DARPA Risk Matrix – Undue Foreign Influence COI or COC (Dec 2021)
- ARRP Risk Matrix – Identified Specific Actions of the Senior/Key Personnel
Research Security Training
Please visit the Research Policies & Related Training page for required Research Security Program trainings.
last updated 11.15.2023